SyncSafe Replication Configuration Types
Supported Configs
SyncSafe Replication is an exceptionally flexible product that can be used in a wide variety of network configurations. To implement SyncSafe Replication effectively, it is important to understand the possible configuration options and their relative benefits. SyncSafe Replication configurations can be used independently or in varying combinations.
These configurations include:
- One to one, active/standby
- One to one, active/active
- Many to one
- One to many
- Chained
- Single server
Note: Not all types of jobs support all of these configurations. See the requirements of each job type to determine which configurations are supported.
Configuration Type: One to One, Active/Standby

Description
One target server, having no production activity, is dedicated to support one source server. The source is the only server actively replicating data.
Applications
- This configuration is appropriate for offsite disaster recovery, failover, and critical data backup. This is especially appropriate for critical application servers such as Exchange, SQL Server, and web servers.
- This is the easiest configuration to implement, support, and maintain.
Considerations
- This configuration requires the highest hardware cost because a target server is required for every source server.
- You must pause the target when backing up database files on the target.
Configuration Type: One to One, Active/Active
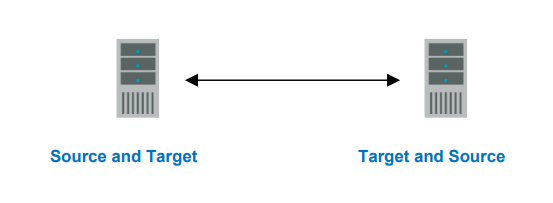
Description
Each server acts as both a source and target actively replicating data to each other
Applications
This configuration is appropriate for failover and critical data backup. This configuration is more cost-effective than the Active/Standby configuration because there is no need to buy a dedicated target server for each source. In this case, both servers can do full-time production work.
Considerations:
- Coordination of the configuration of OpenText Availability and other applications can be more complex than the one to one active/standby configuration.
- During replication, each server must continue to process its normal workload.
- Administrators must avoid selecting a target destination path that is included in the source’s protected data set. Any overlap will cause an infinite loop.
- To support the production activities of both servers during failover without reducing performance, each server should have sufficient disk space and processing resources.
- Failover and failback scripts must be implemented to avoid conflict with the existing production applications.
- You must pause the target when backing up database files on the target.
Configuration Type: Many to One

Description
Many source servers are protected by one target server.
Applications
This configuration is appropriate for offsite disaster recovery. This is also an excellent choice for providing centralized tape backup because it spreads the cost of one target server among many source servers.
Considerations
- The target server must be carefully managed. It must have enough disk space and RAM to support replication from all of the source systems. The target must be able to accommodate traffic from all of the servers simultaneously.
- If using failover, scripts must be coordinated to ensure that, in the event that the target server stands in for a failed server, applications will not conflict.
- You must pause the target when backing up database files on the target.
Configuration Type: One to Many
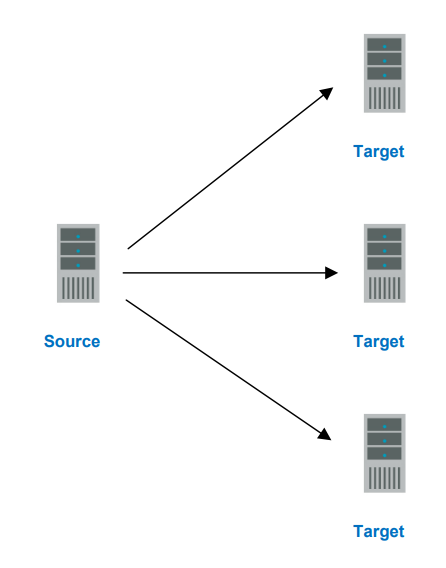
Description
One source server sends data to multiple target servers. The target servers may or may not be accessible by one another.
Applications
This configuration provides offsite disaster recovery, redundant backups, and data distribution. For example, this configuration can replicate all data to a local target server and separately replicate a subset of the mission-critical data to an offsite disaster recovery server.
Considerations
- Updates are transmitted multiple times across the network. If one of the target servers is on a WAN, the source server is burdened with WAN communications.
- You must pause the target when backing up database files on the target.
- If you failover to one of the targets, the other targets stop receiving updates.
Configuration Type: Chained Replication
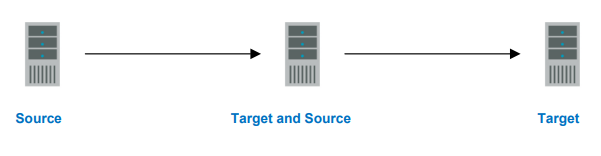
Description
The source server sends replicated data to a target server, which acts as a source server and sends data to a final target server, which is often offsite.
Applications
This is a convenient approach for integrating local high availability with offsite disaster recovery. This configuration moves the processing burden of WAN communications from the source server to the target/source server. After failover in a one to one, many to one, or one to many configuration, the data on the target is no longer protected. This configuration allows failover from the first source to the middle machine, with the third machine still protecting the data.
Considerations
- The target/source server could become a single point of failure for offsite data protection.
- You must pause the target when backing up database files on the target.
Important Implementation Considerations
Evaluate your configuration and the supported functionality of your particular applications when evaluating application replication. Microsoft SQL, File Servers, Active Directory Domain Controllers, DNS Servers, and other similar systems have integrated replication and redundancy technologies and topologies that allow greater automated control over replication and redundant functionality, as well as more consistent live application data replication.
It is recommended that vendor-provided clustering, replication, and availability group technologies be employed to take full advantage of those feature sets over third-party replication options. The use of SyncSafe Replication for this type of operation is useful and recommended in cases where the standard redundancy and replication functions provided by the application vendor cannot be used.