SyncSafe Replication Overview
Overview
SyncSafe Replication offers a tool that brings the workload replication concept of an Availability Group or distributed cluster to any workload running on Linux and Windows.
With this tool, you can:
- Replication critical systems to an alternative server that can be failed over and made active in the event of a failure of the original server.
- Provide VSS-based historical system state checkpoints from which the machine can be recovered.
- Actively replicate specific files/folders/datasets independent of the entire system, enabling data parity between servers.
This tool can be combined with other features and functions to fit a variety of business continuity strategies.
Note
While the Carbonite OpenText tool which powers SyncSafe Replicate offers a wide variety of functionality, not all functions and scenarios have been tested and validated for use in the US Signal environment as part of the SyncSafe Replicate product and may not be supported by US Signal.
Note on Linux Compatibility
While the SyncSafe Replication system, powered by Carbonite OpenText, does offer Linux compatibility, its features and limitations are still being evaluated. We will update our guides with additional documentation specifically for Linux systems as we complete evaluation and documentation of its capabilities and functionality. Please see the Linux Compatibility page for updates and details.
Please Note: While the Carbonite OpenText tool which powers SyncSafe Replication offers a wide variety of functionality, not all functions and scenarios have been tested and validated for use in the US Signal environment as part of the SyncSafe Replication product and may not be supported by US Signal.
Using the SyncSafe Replication tool to protect your systems is simple. You identify what you want to protect on your production server, known as the source, and replicate that to a backup server, known as the target. The target server, on a local network or at a remote site, stores a replica copy of the data from the source. SyncSafe Replication monitors any changes to the source and sends the changes to the replica copy stored on the target server. By replicating only the file changes rather than copying an entire file, SyncSafe Replication allows you to more efficiently use resources.
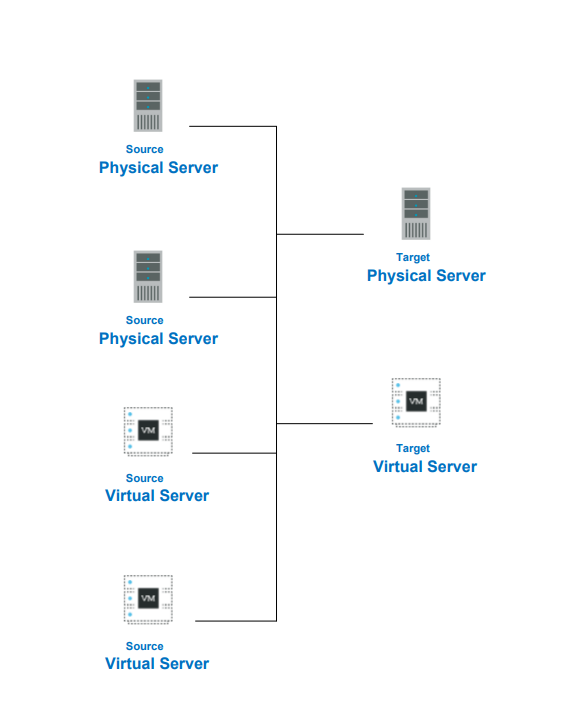
Components
SyncSafe Replication consists of four main components:
- Management Console - A system, preferably a Virtual Machine in your environment, that will manage licenses, replication jobs, and failover tasks for all of the protected workloads in your organization.
- Source - Any system from which you are replicating data or the system state.
- Production Target - The Virtual Machine to which you are replicating data.
- Test Target - For system state replication testing only. This Virtual Machine is separate from the Production Target and is used specifically to test the failover of your production system state without disrupting replication to the production target.
Core Operations
SyncSafe Replication performs three basic types of operations:
- Mirroring — The initial copy or subsequent resynchronization of selected data
- Replication — The on-going capture of byte-level file changes
- Failover — The ability to stand-in for a server, in the event of a failure
Mirroring
Mirroring is the process of transmitting user-specified data from the source to the target so that an identical copy of data exists on the target. When SyncSafe Replication initially performs mirroring, it copies all of the selected data, including file attributes and permissions. Mirroring creates a foundation upon which SyncSafe Replication can efficiently update the target server by replicating only file changes.
If subsequent mirroring operations are necessary, SyncSafe Replication can mirror specific files or blocks of changed data within files. By mirroring only files that have changed, network administrators can expedite the mirroring of data on the source and target servers. Mirroring has a defined end point when all of the selected files from the source have been transmitted to the target. When a mirror is complete, the target contains a copy of the source files at that point in time.
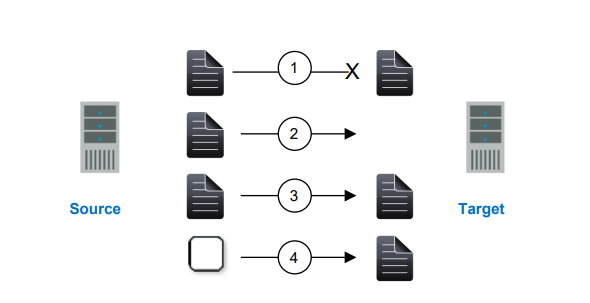
- Identical files are not mirrored.
- New files are mirrored.
- Different files can be mirrored.
- Checksums can calculate blocks of data to be mirrored.
Replication
Replication is the real-time transmission of file changes. Unlike other related technologies, which are based on a disk driver or a specific application, the SyncSafe Replication replication process operates at the file system level and is able to track file changes independently from the file’s related application. In terms of network resources and time, replicating changes is a more efficient method of maintaining a real-time copy of data than copying an entire file that has changed.
After a source and target have been connected through SyncSafe Replication, file system changes from the user-defined data set are tracked. SyncSafe Replication immediately transmits these file changes to the target server. This real-time replication keeps the data on the target up-to-date with the source and provides high availability and disaster recovery with minimal data loss. Unlike mirroring which is complete when all of the files have been transmitted to the target, replication continuously captures the changes as they are written to the source. Replication keeps the target up to date and synchronized with the source.
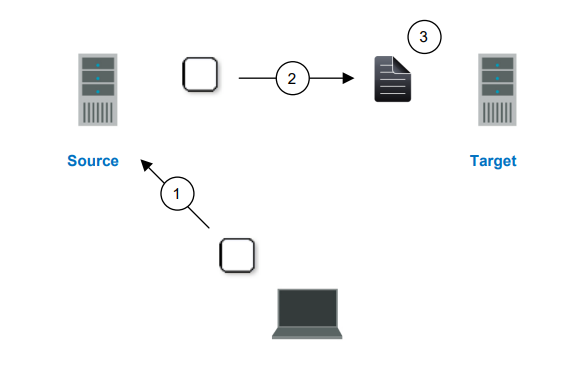
- A user or application updates part of a file.
- Only the changed portion of the file is replicated to the target.
- An up-to-date copy of the file is maintained on the target.
Failover
Failover is the process in which a target stands in for a failed source. As a result, user and application requests that are directed to the failed source are routed to the target.
SyncSafe Replication monitors the source status by tracking requests and responses exchanged between the source and target. When a monitored source does not respond to the target's requests, SyncSafe Replication assumes that the server has failed. SyncSafe Replication then prompts the network administrator to initiate failover, or, if configured, it occurs automatically. The failover target assumes the identity of the failed source, and user and application requests destined for the source server or its IP address(es) are routed to the target.
When partnered with the SyncSafe Replication data replication capabilities, failover routes user and application requests with minimal disruption and little or no data loss.
- User and application requests are sent to the source name or IP address.
- Data on the source is mirrored and replicated to the target.
- The target monitors the source for failure.
- In the event the source fails, the target stands in for the source. User and application requests are still sent to the source name or IP address, which are now running on the target.